Malware Analysis
Every so often someone on crypto-twitter, will reach out and ask if I'd like to beta test or moderate a game in exchange for pay. Usually these are pretty shady and sound too good to be true. Once in a while I'll indulge them and play along. They typically direct me to a website, where I enter a code to access their "game".
I subsequently receive a download, typically a disk image. Upon (safely) extracting the image, more often than not, I'm presented with a .app file.
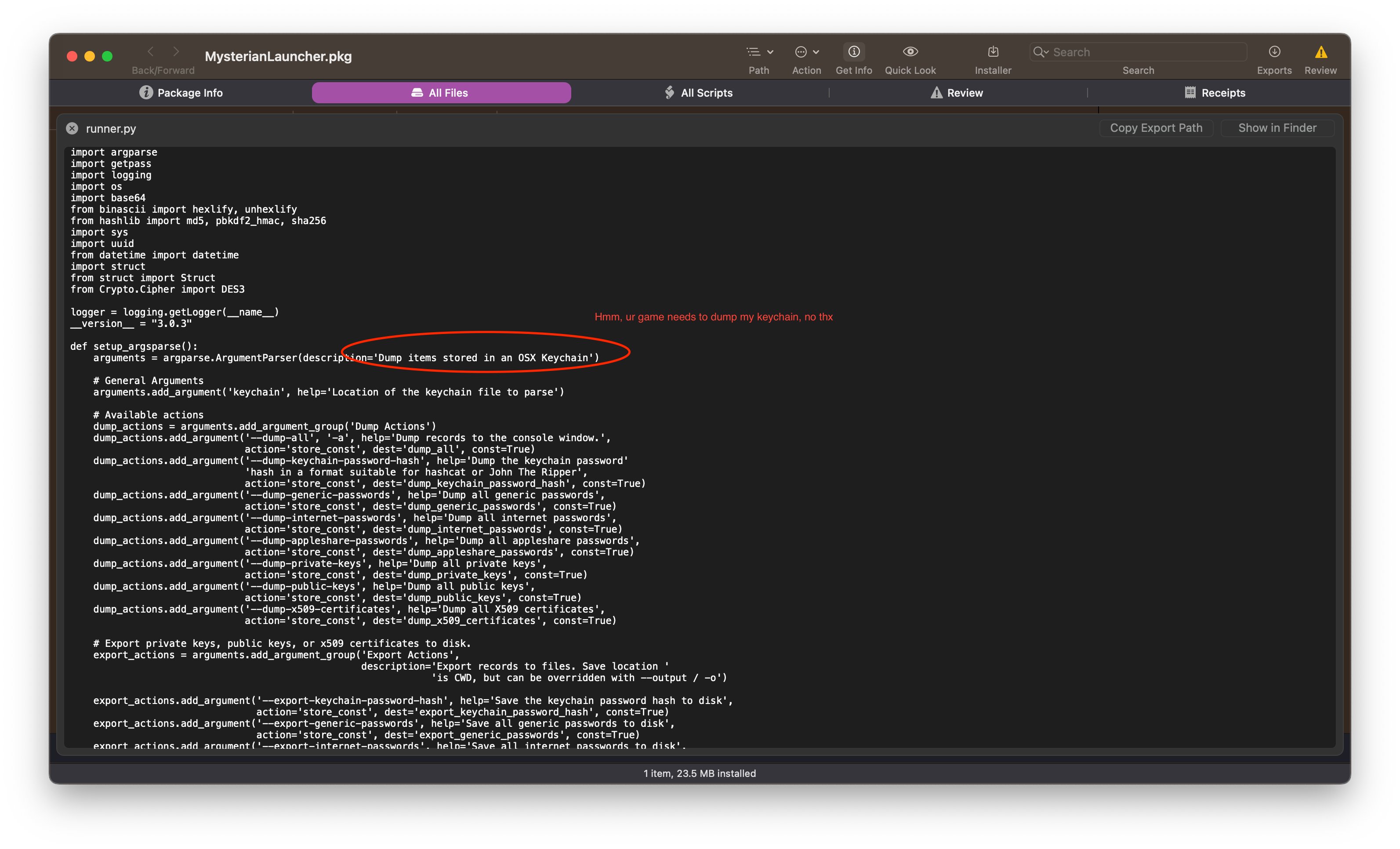
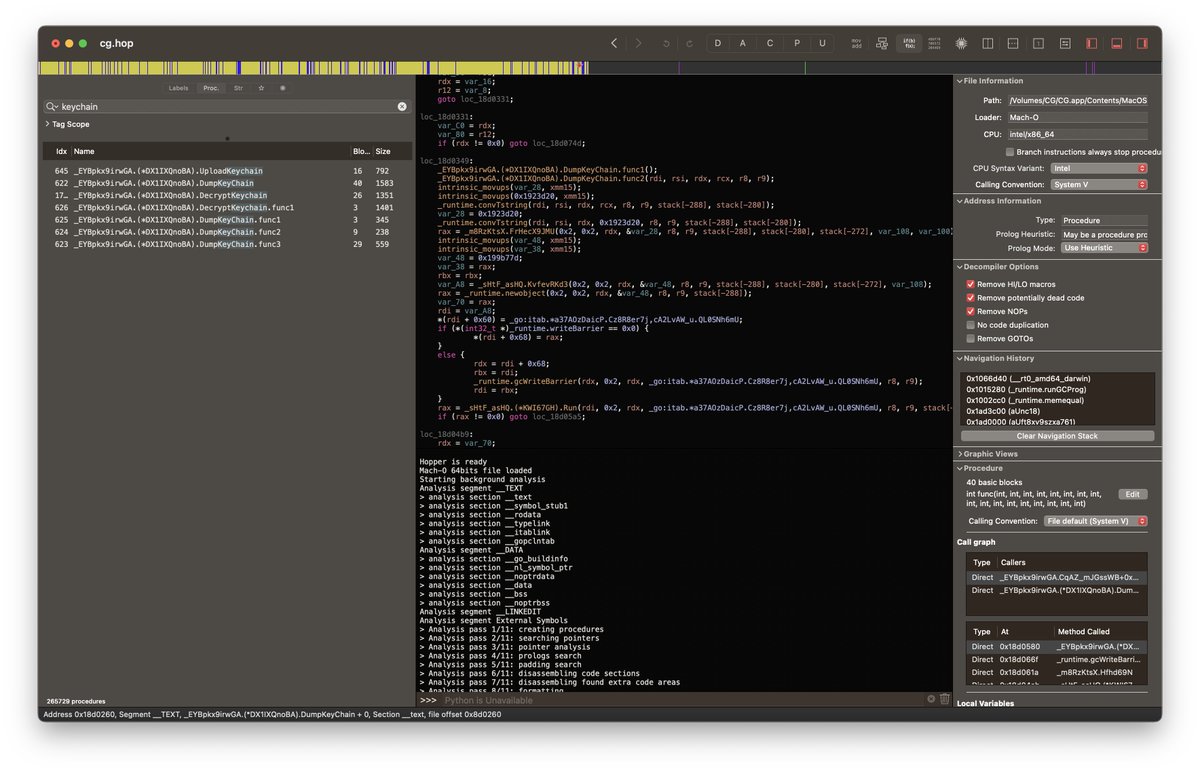
I'll then dump the strings, and examine the binary in Hopper, a reverse engineering tool allowing me to examine the Assembly code, and see if I can spot anything suspicious. Sometimes there are suspicious looking functions (like "dump keychain" or "decrypt keychain"), other times the code is obfuscated and its symbols stripped. Occasionally there is just a raw python script sitting in there in plain sight. Often hidden within these malicous apps are info stealers, a type of malware designed to steal cryptocurrency, credentials, or other sensitive information. Info stealers need to exfiltrate the data they're attempting to steal, and they typically do this by making HTTP requests to remote servers, sometimes using services like telegram, discord, or even self-hosting a web server (also known as a c2, or command and control server). I've even seen things like Sentry being used to report telemetry data back to the attacker.
Subsequently, I'll often hand the samples off to researchers for further analysis & documentation, and more often than not, they'll be able to identify the malware family and provide a writeup.